Research
Research · 07. May 2023
To better understand the connection between NFTs and far-right extremist content, we collected 7.5k NFT and their metadata from 11 blockchains. Categorizing the NFT by their title, description, details and visual assessment of the downloaded images/GIFs/videos, we conclude that far-right extremist content is spread via NFTs on different blockchains.
Research · 13. October 2022
To better understand the connection between NFTs and (far-right) extremist content, we collected 7.5k NFT and their metadata from 11 blockchains. Categorizing the NFT by their title, description, details and visual assessment of the downloaded images/GIFs/videos, we conclude that far-right extremist content is spread via NFTs on different blockchains. Looking at the metadata and images of pre-selected 4.5k NFT from a keyword search, only a small share of NFTs is clearly extremist (2%).
Research · 14. September 2021
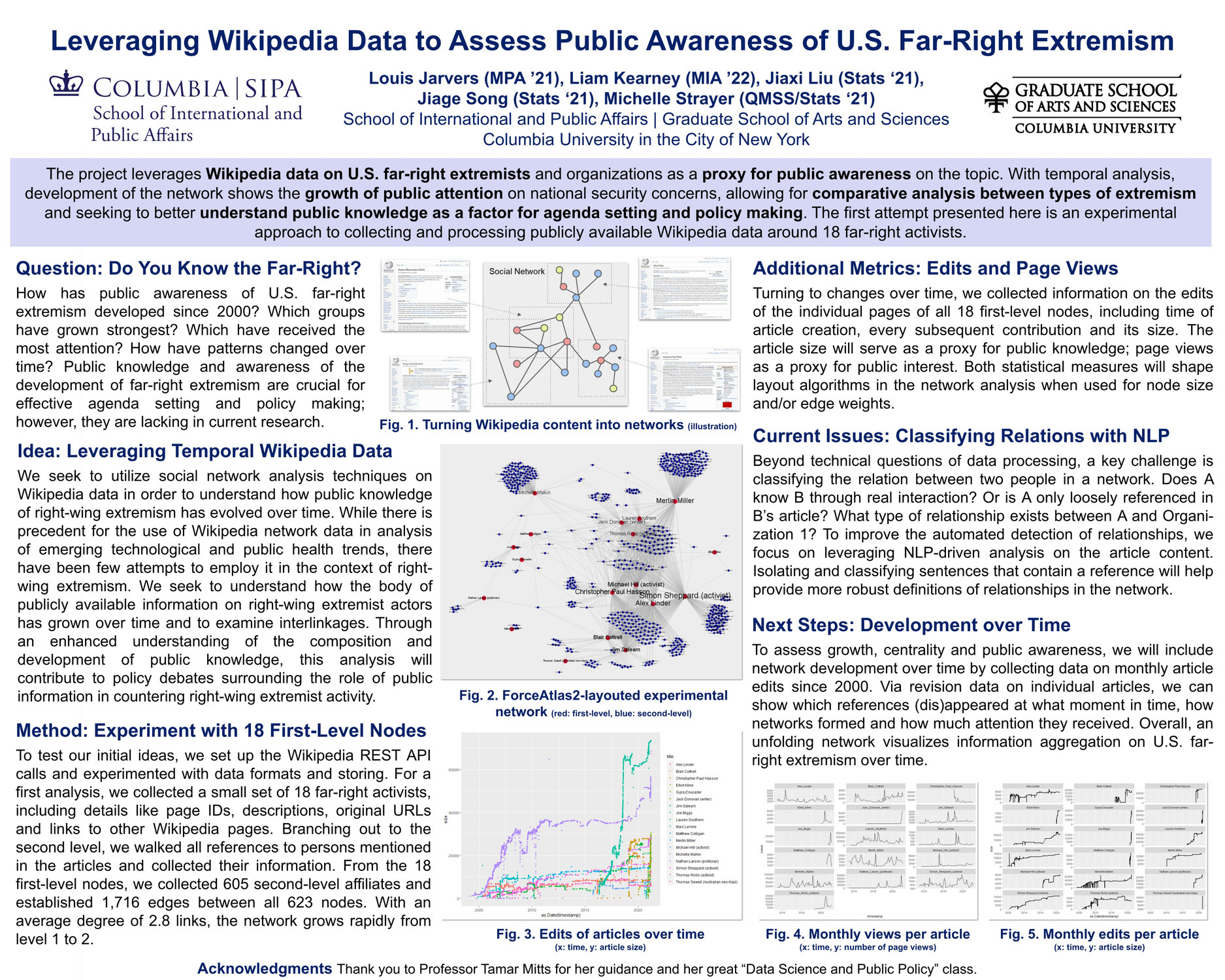
The project leverages Wikipedia data on U.S. far-right extremists and organizations as a proxy for public awareness on the topic. With temporal analysis, development of the network shows the growth of public attention on national security concerns, allowing for comparative analysis between types of extremism and seeking to better understand public knowledge as a factor for agenda setting and policy making. The first attempt presented here is an experimental approach.
Research · 18. February 2021
"CYsyphus" (pronounced SIGH-si-fis) is a decision-support tool, that provides users with an easy-to-search online database on existing cyber reports and recommendations. CYsyphus facilitates the discovery of past wisdom to avoid repetition and enable leapfrogging to new insights and recommendations in support of policy makers, congressional staffers, journalists and students.
Research · 28. December 2020
Addressing interactions and limitations, this article compares structural and activity-related differences between intelligence organizations of states and violent non-state actors (VNSA) and seeks to provide explanations and effects of the distinct setup.
Research · 27. December 2020
The First Battle of Bull Run in the American Civil War (1861), the Battle of Tannenberg in World War I (1914), the Battle of Midway in the Pacific War (1942), the Inchon Landing on the Korean peninsula (1950) or the Six-Day War around Israel (1967) – these are a few of the numerous examples where undoubted, heard and understood intelligence played a decisive role in violent conflicts. This article explains key factors to improve intelligence receptivity.
Research · 22. December 2020
The case of the 2016 German Foreign Intelligence Reform and the following constitutional complaint show one of these rare examples of well-aligned legal advocacy in a field where Human Rights’ defenders are usually bound by the intelligence agencies’ good will to cooperate. After a brief introduction to the field of Human Rights and intelligence, the article focuses on the lawsuit against the 2016 reform, provides an analysis of the advocacy strategy and closes with lessons learned.
Research · 14. December 2020
All-source intelligence analysts need improved modeling, analytic tools, and data visualization in order to understand dense urban areas and enhance situational awareness more effectively. POLassist helps you understand location data in an urban areas to improve situational awareness and response allocation. The POLassist prototype was developed as part of "Hacking4Defense" at Columbia University in the City of New York, 2020.
Research · 03. December 2020
Throughout the years, the skyrocketing need for privacy developed into a race between those who sought for anonymity and those who have a profound interest to see through the privacy barriers. One famous instrument in the privacy toolbox is the decentralized, layered encryption approach of the “The Onion Router”, widely known as “Tor”.
Research · 29. September 2020
The File Transfer Protocol, widely know as FTP, serves a prime example of one of the oldest Internet protocols that have initially been designed for smaller-scale purposes, therefore posed major security risks, and have eventually been developed further to account for the unforeseeable scale that the Internet is nowadays working on.